API: 核心类型¶
Corda provides several more core classes as part of its API.
Corda 提供了以下更多的几个核心类作为它的 API 的一部分。
SecureHash¶
The SecureHash class is used to uniquely identify objects such as transactions and attachments by their hash.
Any object that needs to be identified by its hash should implement the NamedByHash interface:
SecureHash 类被用来唯一标识对象,比如用他们的哈希值来标识 transactions 和 attachment。任何需要使用它的哈希值来唯一标识的都应该实现 NamedByHash 接口:
/** Implemented by anything that can be named by a secure hash value (e.g. transactions, attachments). */
interface NamedByHash {
val id: SecureHash
}
SecureHash is a sealed class that only defines a single subclass, SecureHash.SHA256. There are utility methods
to create and parse SecureHash.SHA256 objects.
SecureHash 是一个封闭的类,它只定义了一个子类 SecureHash.SHA256。这里有一些 utility 方法来创建和转换 SecureHash.SHA256 对象。
CompositeKey¶
Corda supports scenarios where more than one signature is required to authorise a state object transition. For example: “Either the CEO or 3 out of 5 of his assistants need to provide signatures”.
Corda 支持要求多于一个的签名来批准一个 state 对象的交换。比如:“要么 CEO 提供签名,要么他的5个秘书中的3个提供签名”。
This is achieved using a CompositeKey, which uses public-key composition to organise the various public keys into a
tree data structure. A CompositeKey is a tree that stores the cryptographic public key primitives in its leaves and
the composition logic in the intermediary nodes. Every intermediary node specifies a threshold of how many child
signatures it requires.
这个可以通过使用一个 CompositeKey 来实现,这个会使用公钥的组合来将不同的公钥变为一个树状的数据结构。一个 CompositeKey 是一个树状结构,它将加密的公钥的原始数据存储在了它的叶子节点,然后组合的逻辑在中间节点。每一个中间节点指定了一个临界值,这个临界值标识它需要多少个子节点的签名。
An illustration of an “either Alice and Bob, or Charlie” composite key:
一个表示 “或者 Alice 和 Bob,或者是 Charlie” 的组合键:
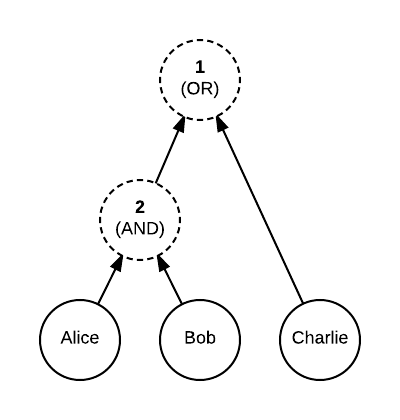
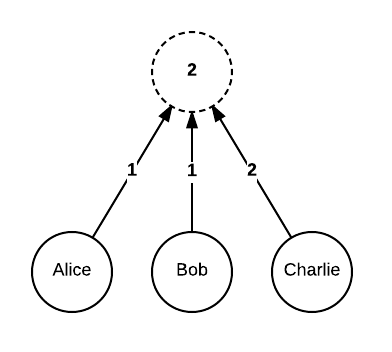
To allow further flexibility, each child node can have an associated custom weight (the default is 1). The threshold then specifies the minimum total weight of all children required. Our previous example can also be expressed as:
为了进一步的灵活性,每个子节点可以有一个相关的自定义 权重*(默认是1)。这个 *临界值 会指定所有的子节点要求至少总权重要达到多少。我们前一个例子也可以按照下边的表示:
Signature verification is performed in two stages:
- Given a list of signatures, each signature is verified against the expected content.
- The public keys corresponding to the signatures are matched against the leaves of the composite key tree in question, and the total combined weight of all children is calculated for every intermediary node. If all thresholds are satisfied, the composite key requirement is considered to be met.
签名的验证经过两步骤:
1. 给定一个签名列表,每个签名跟期望的内容进行比对 1. 签名对应的公钥会跟有关的组合键树结构的叶子节点匹配,并且所有子节点的总合并的权重会为每个中间节点而被计算。如果所有的临界值都满足,组合键的要求就被认为是满足的。